Data Minimization Strategies for GDPR Compliance
Discover effective data minimisation strategies to ensure GDPR compliance, reduce risks, cut costs, and build customer trust while maintaining business functionality.


This report provides a comprehensive analysis of data minimization as a cornerstone of GDPR compliance. It defines the principle, explores its intricate connections with other GDPR tenets, and outlines the significant strategic advantages it offers beyond mere regulatory adherence. The discussion delves into practical implementation strategies, highlights key supporting technologies, addresses common challenges, and draws lessons from real-world case studies and regulatory enforcement actions. Ultimately, the report positions data minimization not just as a legal obligation but as a strategic imperative for fostering trust, enhancing security, and driving operational efficiency in the modern data landscape.
Introduction to Data Minimization under GDPR
Data minimization stands as a fundamental principle enshrined within the General Data Protection Regulation (GDPR), designed to impose strict limits on the collection and processing of personal data. This core tenet dictates that organizations should only acquire and handle personal data that is truly essential for explicitly defined purposes. It forms a cornerstone of privacy-by-design methodologies and is an indispensable component for any entity striving to establish robust data protection practices.
Defining Data Minimization: Core Concepts
The principle of data minimization mandates that data controllers must limit the collection of personal information to precisely what is "directly relevant and necessary to accomplish a specified purpose". This directive extends beyond mere collection to encompass the duration of data retention, stipulating that data should be kept "only for as long as is necessary to fulfil that purpose". This means that organizations should acquire only the personal data they genuinely require and retain it for no longer than its operational utility dictates.
Article 5(1)(c) of the GDPR explicitly articulates this principle, stating that personal data must be "adequate, relevant and limited to what is necessary in relation to the purposes for which they are processed". This core definition can be broken down into three essential points:
Adequacy: The data collected must be sufficient to properly fulfill the stated purpose. It must provide enough information to achieve the intended objective without being incomplete or misleading.
Relevance: The data must possess a rational and direct link to the purpose for which it is being processed. Irrelevant data, even if seemingly innocuous, falls outside the scope of this principle.
Necessity: Organizations must not hold more data than what is strictly needed for that purpose. This prohibits the collection of superfluous information.
A critical aspect of this principle is its discouragement of the speculative collection of personal data. Organizations are explicitly advised against gathering information on the "off-chance that it might be useful in the future". This proactive stance aims to prevent unnecessary data accumulation and the associated risks.
The Foundational Role of Data Minimization within GDPR's Principles
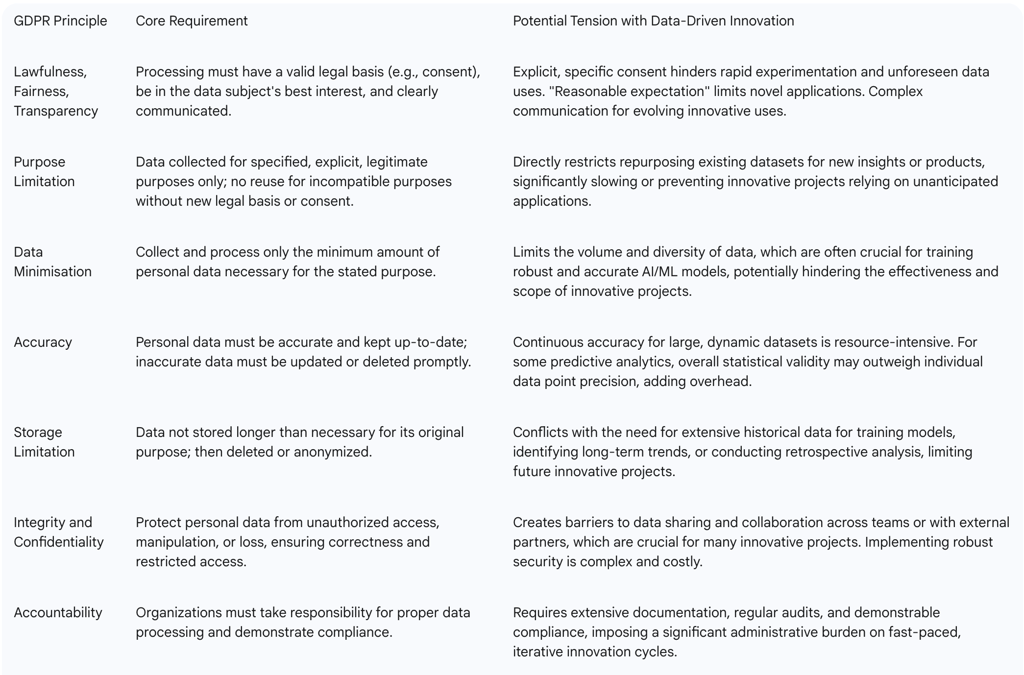
Data minimization is not an isolated requirement but rather one of the seven core data protection principles under the GDPR. These principles collectively form a comprehensive framework for responsible data handling. The other principles include lawfulness, fairness, and transparency; purpose limitation; accuracy; storage limitation; integrity and confidentiality (security); and accountability. The interdependency of these principles means that effective adherence to data minimization naturally supports compliance across the entire GDPR framework.
A deeper examination of the term "adequacy" within data minimization reveals a crucial nuance. While the principle generally emphasizes collecting less data, the term "adequate" means that the data collected must also be sufficient to properly fulfill the stated purpose. If the data gathered is insufficient to achieve the intended objective, it is considered inadequate, which itself constitutes a breach of the data minimization principle. This implies that organizations must perform a precise calibration, ensuring they collect precisely the right amount of data—neither too much nor too little—to fulfill their specified purpose. This careful balance is vital to prevent under-collection, which could hinder legitimate operations, while simultaneously preventing over-collection, which poses inherent privacy risks.
Historically, many organizations operated under the belief that "the more data you have the more valuable it is". The GDPR's data minimization principle fundamentally challenges this traditional perspective. It establishes a baseline assumption that personal data cannot be collected or processed unless certain specific conditions are met. This represents a significant paradigm shift, moving organizations away from a "collect all" mentality towards a disciplined, purpose-driven approach to data handling. This transformation redefines the concept of "value" to encompass the reduced risk and increased trust that are inherently associated with responsible data practices. Embracing this shift requires a profound cultural and operational change within organizations.
Core Principles of Data Minimization and Interconnections
Data minimization is not a standalone concept but is intrinsically linked to and reinforces other fundamental GDPR principles. Understanding these interdependencies is crucial for comprehensive and effective compliance. The collective application of these principles creates a cohesive and robust framework for data protection.
Purpose Limitation
The principle of purpose limitation dictates that personal data must be collected for "specified, explicit, and legitimate purposes" and not processed further in a manner incompatible with those initial purposes. This principle is designed to prevent "function creep," where data initially collected for one reason is later repurposed for unrelated or broader uses without proper justification or consent.
Data minimization serves as the practical application of purpose limitation. It ensures that only the data strictly necessary to fulfill those defined purposes is collected. For instance, an online shop collecting customer names, shipping addresses, and email addresses for order fulfillment would adhere to data minimization by avoiding the collection of unnecessary data like ID numbers, as these are not relevant to the core purpose of processing the order.
Storage Limitation
Storage limitation mandates that personal data should be kept "no longer than is necessary for the purposes for which the personal data are processed". This principle necessitates the establishment of a strict data retention policy within organizations.
Data minimization is crucial for effective adherence to storage limitation. By collecting only essential data from the outset, there is inherently less data to store and manage over retention periods. This proactive reduction in data volume simplifies the entire data lifecycle management. Furthermore, regularly reviewing and securely deleting outdated or redundant data prevents unnecessary exposure and aligns seamlessly with both principles.
Lawfulness, Fairness, and Transparency
This principle requires that personal data be processed legally, fairly, and in a transparent manner. A key component of transparency involves clearly communicating data processing purposes to data subjects.
Data minimization directly supports lawfulness and fairness by ensuring that data is collected solely for legitimate purposes. Transparency is significantly enhanced when organizations are upfront about precisely why they need specific data, which in turn builds trust with data subjects. When less data is collected, it becomes inherently simpler to demonstrate that the processing is both lawful and fair.
Accuracy
The accuracy principle mandates that personal data must be accurate and, where necessary, kept up to date. Any inaccurate data must be rectified or erased without undue delay.
While not a direct component of data minimization, collecting less data can indirectly contribute to accuracy. With a smaller, more focused dataset, it becomes easier for organizations to maintain the accuracy and up-to-date nature of the information. The individual's right to rectification , which allows them to complete incomplete data, can also serve as an indicator that the data held may be inadequate for its purpose.
Integrity and Confidentiality (Security)
This principle requires that personal data be handled securely to prevent unauthorized access, loss, or damage. This necessitates the implementation of robust safeguards and cybersecurity measures.
Data minimization significantly enhances data security. Every piece of personal data collected increases potential vulnerabilities and expands the "attack surface" for cyber threats. By limiting data collection to the minimum required, businesses reduce their chances of data breaches and minimize the impact should an incident occur.
Accountability
The accountability principle places the responsibility on organizations to demonstrate compliance with all GDPR principles. This is not a passive requirement but involves active governance, thorough documentation, and the implementation of appropriate technical controls.
Data minimization is a key component of accountability. By implementing and documenting data minimization practices—such as conducting data audits, defining clear purposes for data collection, and establishing robust retention policies—businesses can effectively demonstrate their commitment to responsible data handling and adherence to the regulation. A smaller, well-defined dataset is inherently easier to protect, manage, and defend during an audit.
The principles outlined above are not intended to be implemented in isolation; rather, they exhibit a synergistic effect. For instance, defining a clear purpose for data processing (purpose limitation) directly dictates what data is necessary (data minimization) and how long it should be kept (storage limitation). This in turn simplifies security measures (integrity and confidentiality) because there is less data to protect. This interconnectedness means that a holistic approach, where data minimization is integrated into the design of all data processing activities, naturally supports compliance with the other principles, leading to more robust and efficient data governance.
The accountability principle serves as a powerful enabler of data minimization. It requires organizations to demonstrate compliance, which is an active rather than passive obligation. To effectively demonstrate adherence to data minimization, organizations must maintain clear records of what data is collected, the reasons for its collection, how long it is retained, and how it is secured. This inherent need for comprehensive documentation and auditable processes effectively compels the rigorous implementation of data minimization strategies. Accountability thus transforms data minimization from a mere suggestion into an operational imperative, where the burden of proof rests with the controller, making proactive and auditable data minimization practices essential for avoiding regulatory scrutiny and potential penalties.

Strategic Benefits of Data Minimization (Beyond Compliance)
While achieving GDPR compliance is a fundamental driver for implementing data minimization, its advantages extend significantly beyond merely avoiding regulatory penalties. This principle offers substantial strategic benefits that contribute to an organization's overall resilience, operational efficiency, and competitive standing in the market.
Enhanced Data Security and Reduced Risk
A critical advantage of data minimization lies in its direct impact on cybersecurity. Every piece of personal data collected inherently increases potential vulnerabilities and expands the "attack surface" that can be exploited by cyber threats. By rigorously limiting data collection to the absolute minimum required, businesses can significantly reduce their chances of experiencing data breaches and, crucially, minimize the potential impact should a breach occur. Less data translates directly to less sensitive information at risk, thereby reducing the severity of potential data loss and the subsequent financial and reputational damage. This approach fosters a proactive posture towards data security, cultivating heightened vigilance throughout the organization.
Operational Efficiency and Cost Savings
The practice of collecting and storing only necessary data yields tangible benefits in terms of operational efficiency and cost reduction. It significantly lowers storage and management expenses associated with vast data volumes. With less data to process, analyze, and prune, organizations can manage their information more effectively, leading to improved overall operational efficiency. Furthermore, streamlined data management facilitates faster responses to data subject access requests (DSARs), as there is a smaller, more manageable dataset to sort through and retrieve information from.
Improved Data Quality and Analytics
Eliminating the collection of unnecessary, redundant, obsolete, or trivial (ROT) data naturally leads to a substantial improvement in the quality and accuracy of the remaining datasets. By focusing resources on relevant and necessary data, organizations cultivate cleaner, more reliable datasets. This enhanced data quality, in turn, enables more accurate and meaningful analytics and insights, allowing for better-informed decision-making.
Increased Customer Trust and Loyalty
In an era of heightened privacy awareness, protecting customer data privacy through data minimization is paramount for maintaining an organization's reputation and demonstrating its commitment to privacy. This commitment fosters increased customer loyalty and approval. Transparency about data practices and collecting only what is genuinely expected by consumers builds significant trust.
Preparedness for Evolving Regulations
Implementing data minimization practices helps businesses streamline compliance with both existing and emerging data privacy regulations across the globe. It establishes a robust and adaptable privacy foundation that makes it easier to adjust to new legal requirements, thereby reducing the burden of future compliance efforts and ensuring long-term regulatory preparedness.
Data minimization, while a compliance baseline, extends its benefits to reduced operational costs, improved efficiency, and enhanced trust. These factors collectively contribute to a stronger market position. In a landscape where consumer privacy awareness is steadily increasing , companies that visibly prioritize data minimization are likely to be favored by consumers. This means that data minimization is no longer merely a compliance cost but a strategic investment that can lead to a competitive advantage, increased customer acquisition, and reduced customer churn. It transforms the perception of privacy from a regulatory burden into a compelling value proposition.
The fundamental premise of data minimization is that "the less data an organization has in its possession, the fewer the opportunities for such data to be misused". This principle applies not only to potential malicious attacks but also to inadvertent mishandling or the pitfalls of "data hoarding". The financial and reputational costs associated with data breaches are substantial. Data minimization, therefore, functions as a fundamental risk mitigation strategy by proactively shrinking the potential "blast radius" of any data incident. It encourages a disciplined approach to data management that inherently reduces organizational liability and strengthens its overall security posture.
4. Practical Strategies for Implementing Data Minimization
Effective implementation of data minimization requires a systematic and continuous approach, integrating privacy considerations into every stage of the data lifecycle. This involves a combination of policy, process, and technological measures.
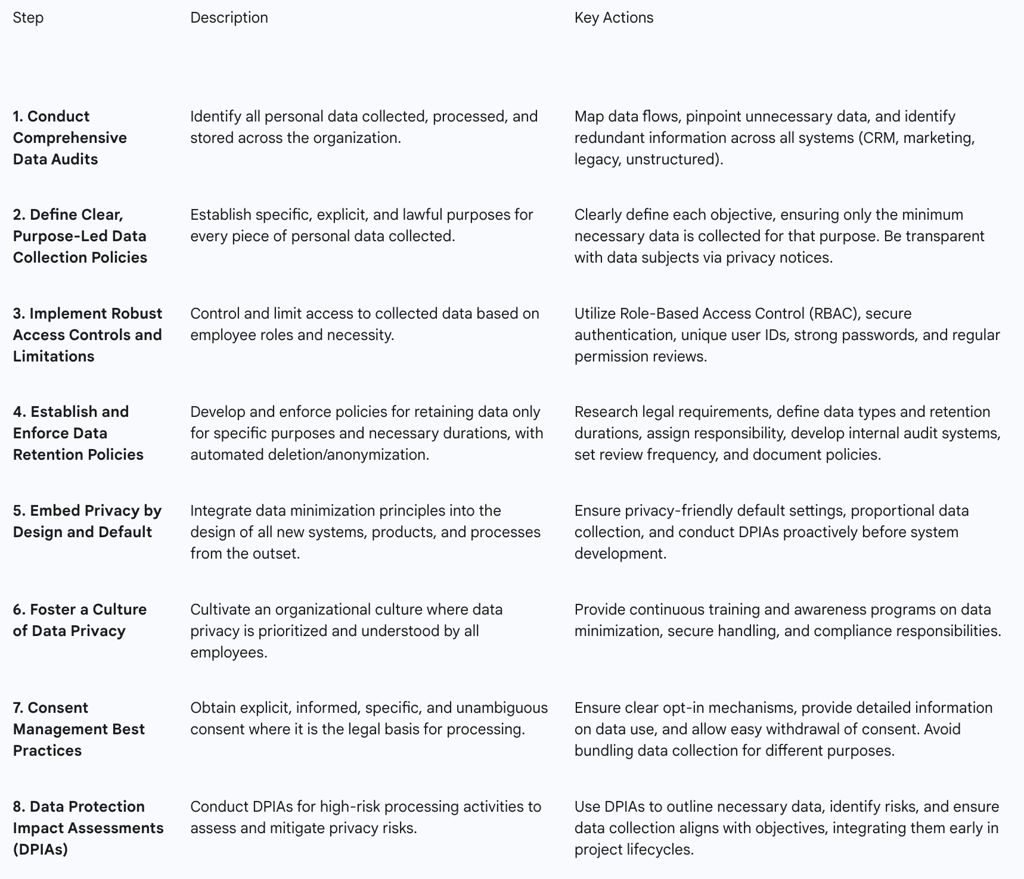
Conducting Comprehensive Data Audits
The foundational step for any data minimization initiative is to conduct a comprehensive data audit. This process involves identifying all personal data collected, processed, and stored across the entire organization. The scope of this audit should include data residing in various systems, such as CRM platforms, marketing tools, legacy systems, and even unstructured formats like documents and emails. The primary purpose of these audits is to identify unnecessary data, pinpoint redundant information, and refine existing data minimization practices. They are essential for gaining a clear understanding of "what data is held" before any effective minimization efforts can begin. Regular data privacy audits are strongly recommended to ensure that data remains adequate, relevant, and limited to its specified purpose on an ongoing basis.
Defining Clear, Purpose-Led Data Collection Policies
Data collection activities must be rigorously guided by specific, explicit, and lawful purposes. Each individual data point collected should serve a clear and stated purpose. To implement this, organizations must clearly define each objective and ensure that only the minimum amount of personal data is collected to achieve that specific purpose. For example, if data is collected for marketing, only information directly related to that marketing purpose should be gathered, rather than broadly capturing all customer behaviors. Transparency with customers about data processing purposes is also vital for building trust. Privacy notices should clearly inform data subjects about how their personal data will be used.
Implementing Robust Access Controls and Limitations
Once data is collected, its access must be carefully controlled and limited based on employees' roles and responsibilities. Only individuals who genuinely require access to specific data for the performance of their duties should be granted it. Role-Based Access Control (RBAC) is a key mechanism for achieving this. Organizations should implement secure authentication practices, including unique user identifiers, strong password policies, and regular reviews of access permissions to remove obsolete or unnecessary privileges.
Establishing and Enforcing Data Retention Policies
A strict data retention policy is a fundamental requirement, ensuring that data is retained only for specific purposes and for no longer than is necessary. Once the defined purposes have been fulfilled or the required retention periods have passed, the data should be securely deleted or anonymized. Practical steps for developing such a policy include:
Team Formation: Designating a team of experts to devise the policy, given the complexity of data retention procedures.
Legal Research: Thoroughly researching all applicable legal and regulatory requirements, such as tax laws or industry-specific mandates, which will form the foundation of the policy.
Data Valuation: Determining the types of data most valuable to the organization to inform appropriate retention durations.
Responsibility Assignment: Nominating a specific department or position responsible for enforcing and regularly updating the policy.
Internal Audits: Developing an internal audit system to help ensure ongoing policy compliance.
Review Frequency: Defining a regular schedule for reviewing and updating the data retention policy to adapt to changing needs and regulations.
Software Implementation: Defining how the data retention policy will be implemented at a software level, including automated deletion processes.
Documentation and Approval: Documenting all determined procedures and guidelines, and presenting the policy to important stakeholders for their approval and necessary revisions.
It is important to note the individual's right to erasure, also known as the "right to be forgotten," which allows data subjects to request the deletion of data that is no longer necessary for its original purpose.
Embedding Privacy by Design and Default
Data minimization principles should be integrated into the design of all new systems, products, and processes from their inception, rather than being treated as an afterthought. This "Privacy by Design" approach means that data collection forms, for example, should be designed to capture only essential information. This is a proactive, not reactive, approach to privacy , involving assessing privacy risks, often through Data Protection Impact Assessments (DPIAs), before building new systems. Additionally, default settings for data sharing, tracking, and permissions should be configured to the most privacy-protective options.
Fostering a Culture of Data Privacy
Technical measures alone are often insufficient without a strong internal data culture. It is crucial that all employees understand GDPR principles and their specific roles in data protection. Regular training sessions are essential to educate employees on how to collect only necessary data, handle data securely, and properly follow data deletion practices. Strong leadership commitment is fundamental for driving this necessary cultural shift.
Consent Management Best Practices
Where consent serves as the legal basis for processing personal data, it must be explicit and informed. Consent must be freely given, specific, informed, and unambiguous, and data subjects must be able to withdraw it easily at any time. From a data minimization perspective, organizations should avoid "bundling in" the collection of personal data for service enhancements with data required for core services; instead, separate choices should be offered to individuals.
Data Protection Impact Assessments (DPIAs)
Data Protection Impact Assessments (DPIAs) are crucial tools for assessing the impact of proposed processing operations on personal data protection, particularly when there is a high risk to individuals' rights and freedoms. A DPIA plays a significant role in data minimization by helping to outline precisely what data is necessary and identifying potential risks in processing activities, thereby ensuring that all collected data aligns with the defined objectives.
The concept of "necessity" in data minimization is not static; it is dynamic and can "differ from one individual to another" or evolve over time. For instance, a small club might initially require only basic member information, but as its membership grows, it may become necessary to collect additional data to properly manage activities and payments. This inherent dynamism means that data minimization is not a one-time policy implementation but requires continuous assessment and adaptation. Organizations must therefore implement mechanisms for periodic review of their data holdings and collection practices. This ensures ongoing compliance and adaptation to changing business needs and data subject interactions.
Achieving robust data minimization requires a multi-faceted, integrated approach that considers policy, technology, and human behavior. Effective implementation involves developing clear policies (e.g., through data audits and defining purposes), deploying technological solutions (e.g., privacy by design, access controls), and addressing human elements (e.g., employee training, fostering a privacy-aware culture). A failure in any one of these areas can undermine the others; for example, excellent policies are ineffective without trained employees to implement them, and advanced technology will not compensate for a lack of clear purpose definitions. Therefore, organizations cannot rely solely on technical fixes or policy documents; they must actively cultivate a privacy-aware culture and ensure continuous alignment across all three pillars.
Key Techniques and Technologies Supporting Data Minimization
Beyond policy and process, various technical measures and privacy-enhancing technologies (PETs) are indispensable for operationalizing data minimization and safeguarding personal data effectively. These tools enable organizations to meet compliance requirements while often preserving data utility for business objectives.
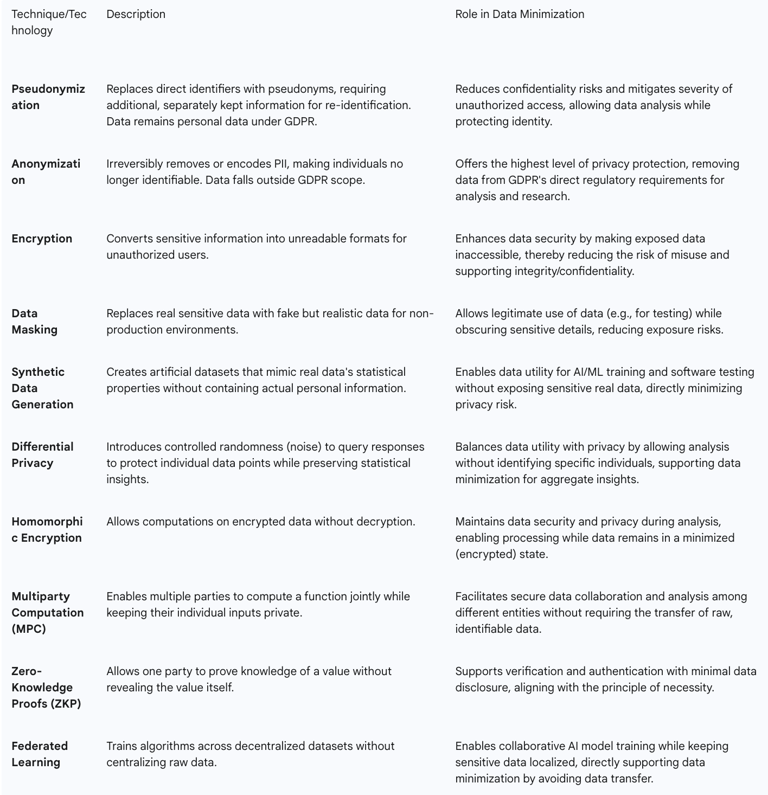
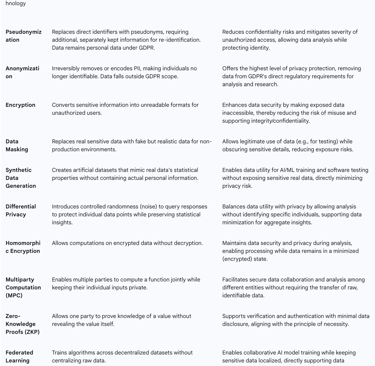
Pseudonymization
Pseudonymization involves processing personal data in a manner that it can no longer be attributed to a specific data subject without the use of additional information. Crucially, this additional information must be kept separately and be subject to robust technical and organizational security measures. This technique is typically reversible, allowing the original data to be retrieved when necessary.
The role of pseudonymization in data minimization is significant: it reduces confidentiality risks by preventing the direct disclosure of identifiers and mitigating the severity of unauthorized access. It enables organizations to perform data analysis and link various records without revealing the personal identity of data subjects. It is important to note that pseudonymized data remains personal data under the GDPR. This means its processing must still comply with all GDPR obligations, including the principles outlined in Article 5. This distinction is critical, as pseudonymization does not remove the data from GDPR's regulatory scope entirely.
Anonymization
Anonymization is the process of irreversibly modifying or removing personally identifiable information (PII) from data, rendering individuals no longer identifiable. This technique provides the highest level of privacy protection.
The primary role of anonymization in data minimization is that fully anonymized data does not qualify as personal data under the GDPR. Consequently, it is not subject to the same restrictions as personal data. This offers greater flexibility for researchers and for various forms of analysis, as the data falls outside the direct scope of GDPR obligations. Common anonymization techniques include data masking, data aggregation, random data generation, data generalization, data swapping, perturbation, suppression, and synthetic data generation.
Encryption
Encryption involves converting sensitive information into an unreadable format for unauthorized users, thereby ensuring data confidentiality during both storage and transmission.
While encryption does not directly reduce the volume of data collected, it is a critical security measure that strongly supports data minimization by rendering exposed data inaccessible to unauthorized individuals. This significantly reduces the risk of misuse even if a breach occurs. It is a key component in upholding the GDPR principle of "Integrity and Confidentiality."
Data Masking
Data masking is a technique where real sensitive data is replaced with fake but realistic data. Its primary application is to protect PII, especially in non-secure environments such as development, testing, or training, where access to actual production data is not appropriate.
Data masking supports data minimization by allowing the legitimate use of data while obscuring sensitive details, thereby reducing the risk of exposure in non-production systems. Techniques include substitution, shuffling, and character or number masking.
Privacy-Enhancing Technologies (PETs)
Privacy-Enhancing Technologies (PETs) encompass a range of tools, techniques, and practices specifically designed to protect individuals' privacy. They achieve this by minimizing personal data use, maximizing data security, and empowering individuals to control their information. PETs embody the principles of privacy-by-design.
PETs play a crucial role in data minimization by allowing organizations to achieve data utility (e.g., for analytics, AI training) while simultaneously minimizing privacy risk. They enable organizations to extract valuable insights and build robust systemswhile maintaining strong privacy protections. Examples of PETs include:
Synthetic Data: Generates artificial datasets that closely mimic the statistical qualities of real-world data without containing any actual personal information. This is particularly useful for AI/ML training and software testing where sensitive data cannot be used.
Differential Privacy: A mathematical method that introduces controlled randomness or "noise" into query responses. This makes it significantly harder to pinpoint individual data points within a dataset while still preserving overall statistical insights for analysis.
Homomorphic Encryption: An advanced cryptographic technique that allows computations to be performed directly on encrypted data without the need for decryption. This enables analysis while the data remains secure and private throughout the process.
Multiparty Computation (MPC): A cryptographic protocol that enables multiple parties to jointly compute a function over their inputs while ensuring that those inputs remain private to each party. This allows for collaborative analysis without sharing raw data.
Zero-Knowledge Proofs (ZKP): A cryptographic method where one party can prove to another that they possess knowledge of a certain value without revealing the value itself. This supports authentication and verification with minimal data disclosure.
Federated Learning: A machine learning approach that trains algorithms across multiple decentralized edge devices or servers holding local data samples, without exchanging them. This allows for collaborative AI model training without transferring raw data to a central location.
Data Management Platforms and Tools
Various software solutions, often referred to as data management platforms or GDPR compliance software, are designed to assist organizations in managing data throughout its lifecycle, thereby supporting GDPR compliance, including data minimization. These platforms typically offer features such as data discovery and mapping , consent management , subject rights management (DSARs) , automation of data retention and deletion , and vendor risk management.
A clear distinction exists between pseudonymization and anonymization. Pseudonymized data, while made harder to link to an individual, remains personal data under the GDPR, meaning all GDPR obligations continue to apply. In contrast, truly anonymized data falls outside GDPR's scope entirely, as individuals are no longer identifiable. This represents a spectrum of de-identification, offering varying levels of risk reduction and compliance burden. Organizations must carefully assess the precise level of identifiability required for their specific processing purposes. Choosing full anonymization where possible can significantly reduce compliance overhead, but if re-identification is ever a necessary future requirement, then pseudonymization is the appropriate choice, albeit with continued GDPR obligations. This decision directly impacts the "necessity" and "limitation" aspects of data minimization.
The tension between maximizing data utility (for analytics, AI development, and personalization) and ensuring robust privacy is a persistent challenge for data-driven organizations. Privacy-Enhancing Technologies (PETs) are explicitly designed to bridge this gap. They allow organizations to extract valuable insights and build sophisticated systems while maintaining strong privacy protections. This represents a significant shift from a historical trade-off between utility and privacy to a model where both can be achieved simultaneously. PETs are not merely compliance tools; they are strategic enablers for data-driven innovation in a privacy-conscious regulatory environment. They empower businesses to maximize the value of their data while inherently embedding data minimization and privacy-by-design principles, fostering trust and reducing risk without compromising functionality.
Addressing Challenges in Data Minimization Implementation
Despite the clear benefits, implementing data minimization is often fraught with complexities. Organizations frequently encounter significant hurdles that necessitate careful navigation and strategic planning to overcome.
Balancing Data Utility with Privacy
One of the most significant challenges in data minimization is striking the right balance between the utility of data and the imperative of privacy. Organizations frequently collect vast amounts of data to drive innovation, enhance customer experiences, and gain competitive advantages. This objective can appear to conflict with the principle of data minimization, which strictly dictates that only essential data should be collected and stored. For example, aggressive anonymization techniques, while enhancing privacy, may inadvertently reduce the usefulness of the data for detailed analysis. The resolution involves adopting a purpose-driven approach, critically evaluating the necessity of each data point against specific, well-defined business objectives. The use of techniques such as generalization, suppression, and perturbation can help achieve this delicate balance between privacy and utility. Furthermore, Privacy-Enhancing Technologies (PETs) are specifically designed to address this very challenge.
Managing Complex Data Ecosystems and Legacy Systems
Modern organizations frequently operate within highly complex data ecosystems, where data is dispersed across multiple systems, various cloud providers, and numerous third-party services. A significant challenge arises from legacy systems, which often were not designed with data minimization in mind, making it difficult to retrofit these principles effectively. To address this, a robust data governance framework becomes essential, encompassing clear policies and procedures for data collection, processing, and retention across the entire organization. Data mapping and discovery tools are invaluable for locating and documenting data flows within these complex environments. Additionally, establishing strong vendor management practices is crucial to ensure that third-party partners adhere to the same data minimization standards.
Overcoming Organizational Resistance to Change
Implementing data minimization often necessitates significant changes to existing processes and systems, which can be met with considerable resistance from employees and stakeholders. This resistance may stem from concerns about the potential impact on established business operations, the perceived complexity of new procedures, a general reluctance to alter ingrained practices, or a deeply entrenched "data hoarding" mentality where more data is mistakenly equated with more value. Overcoming this resistance requires a combination of education, clear communication, and strong leadership. It is important to highlight the tangible benefits of data minimization in terms of privacy, security, and regulatory compliance. Involving key stakeholders in the development of data minimization strategies can help build buy-in, and providing comprehensive training and ongoing support during the implementation phase will further ease the transition.
Identifying and Deleting Unnecessary Data at Scale
Within large and often sprawling datasets, particularly those accumulated from legacy systems, it can be exceptionally difficult to accurately identify and ensure the secure deletion or anonymization of unnecessary data. This practical challenge requires sophisticated solutions. Organizations should leverage tools for data cataloguing, discovery, and classification to efficiently and effectively identify superfluous data. Implementing automated data deletion policies and systems is also critical to ensure that data is removed promptly when it is no longer needed. For legacy data, a thorough data audit is necessary to identify redundant or outdated information that can be purged, and regularly updating data retention policies will help prevent unnecessary data accumulation in the future.
Navigating Evolving Regulatory Landscapes
The global data privacy landscape is in a constant state of flux, with new laws being enacted and existing ones frequently updated. This dynamic environment demands continuous vigilance from organizations to ensure ongoing compliance. To navigate this challenge, organizations must stay informed about new regulations and guidance issued by data protection authorities. Building adaptable privacy programs that can readily extend and adjust as business conditions and regulations evolve is crucial for long-term success. Seeking expert legal support when necessary can provide invaluable guidance in complex or uncertain regulatory scenarios.
The true cost of failing to implement data minimization extends beyond mere regulatory fines. While penalties are a significant consequence of non-compliance , the challenges discussed also highlight other substantial costs. Over-retention of data, for instance, leads to increased storage expenses. More critically, poor data practices erode customer trust, which can result in customer churn and significant reputational damage. This underscores that the true "pitfall" of neglecting data minimization is not solely about avoiding regulatory penalties, but a broader erosion of business value through increased operational costs, diminished data quality, and a damaged brand reputation. This reinforces the strategic imperative of proactive data minimization.
The concept of "data hoarding" is explicitly identified as a significant cultural barrier to data minimization. This suggests that organizational culture can be a major impediment, extending beyond technical or legal understanding to a deeply ingrained habit of collecting and retaining all data "just in case." Effective data minimization therefore requires a fundamental shift in organizational mindset. This means moving away from the belief that "more data is always better" towards a disciplined, purpose-driven approach. Such a transformation necessitates strong leadership, continuous education, and a clear articulation of the benefits that a "lean" data strategy can bring to the organization.
Case Studies and Regulatory Enforcement
Real-world examples and regulatory actions provide concrete illustrations of the importance of data minimization and offer valuable lessons for organizations striving for GDPR compliance.
Illustrative Cases of Non-Compliance and Regulatory Actions
Several cases highlight the consequences of failing to adhere to data minimization principles:
Airbnb (DPC Case Study 20): Airbnb faced regulatory action for violating data minimization by requiring a photo ID from a data subject who requested data deletion, even though no ID had been provided to Airbnb previously. The Data Protection Commission (DPC) deemed this an unnecessary collection of new data without a lawful basis, ordering Airbnb to revise its internal policies. This case underscores that data minimization applies even to the
process of exercising data subject rights. Collecting new, unnecessary data to fulfill a deletion request is a clear violation of the principle.
Amazon France Logistique (CNIL Fine): Amazon France Logistique was fined €32 million by the CNIL (the French data protection authority) for excessive monitoring of its warehouse employees. The company used scanners to track employee productivity and inactivity, a system deemed invasive and a violation of data minimization. The CNIL determined that this extensive collection created undue pressure on employees and provided a competitive advantage at the expense of employee privacy. This example demonstrates that "necessity" is not solely defined by business efficiency or competitive advantage; it must be balanced against individuals' fundamental privacy rights and the proportionality of the data collected relative to the stated purpose. Even if data
could be useful for internal metrics, if its collection is excessive for the explicit purpose, it constitutes non-compliance.
Marriott (FTC Settlement): Marriott experienced a series of data breaches that were significantly exacerbated by a lack of data minimization practices. These breaches exposed millions of guest records, including unencrypted passport numbers. A substantial portion of the exposed data was deemed unnecessary for Marriott to collect or was retained for significantly longer than required. As part of its settlement with the Federal Trade Commission (FTC), Marriott was ordered to create a data minimization policy. This case clearly illustrates the
causal link between poor data minimization practices and magnified breach impact. Over-collection and over-retention directly increase the financial and reputational damage incurred when security incidents occur.
General Fines: Non-compliance with GDPR principles, including data minimization, can lead to substantial financial penalties. Organizations can face fines of up to €20 million or 4% of their total global annual turnover, whichever amount is higher, for severe violations. Less severe infringements can still incur significant fines, up to €10 million or 2% of the preceding financial year's worldwide annual revenue.
Guidance from Data Protection Authorities (ICO, EDPB) on Best Practices
Data protection authorities consistently provide guidance that reinforces data minimization as a core best practice:
ICO Guidance: The UK Information Commissioner's Office (ICO) consistently emphasizes that personal data must be "adequate, relevant and limited to what is necessary". The ICO advises against collecting data speculatively, or on the "off-chance that it might be useful in the future". It strongly recommends periodic reviews of processing activities to ensure that data held remains relevant and adequate, with any unnecessary data being deleted promptly. The ICO also highlights that processing inadequate data (i.e., too little data to fulfill a purpose) can also constitute non-compliance. For employment records, employers are specifically advised to collect and retain only the minimum amount of personal information required and to regularly check the information held for continued relevance. The ICO suggests that proactive compliance, including regular auditing, staff training, maintaining up-to-date policies, and rapid incident response, can significantly mitigate the severity of enforcement actions. Transparency and engagement with the ICO during an investigation can often lead to more favorable outcomes.
EDPB Guidelines: The European Data Protection Board (EDPB) issues general guidance to clarify EU data protection laws and promote a common understanding among organizations. The EDPB recommends that products and services be designed to allow for anonymous use or the least privacy-intrusive methods possible. It stresses the importance of implementing technical and organizational measures, such as those for blockchain technologies, from the earliest design stages. The EDPB advises that storing personal data directly in a blockchain should generally be avoided if it conflicts with fundamental data protection principles. Furthermore, the EDPB provides detailed guidelines on pseudonymization, clarifying its definition, objectives, advantages, and its crucial role in adhering to the data minimization principle.
The case studies, particularly those involving Airbnb and Amazon, demonstrate that regulators are not focused on abstract legal definitions but on how data minimization is applied in real-world operational contexts. Regulators are actively scrutinizing specific data collection practices, such as unnecessary ID requirements or excessive employee monitoring, that extend beyond what is strictly necessary for the stated purpose. This implies that organizations need to move beyond a theoretical understanding of data minimization to a granular assessment of every data point collected, processed, and retained. This requires rigorous internal audits and a critical review of existing systems and workflows to ensure genuine indispensability for explicit purposes.
A complex dynamic exists regarding data minimization and large online platforms. Some analysis suggests that the GDPR, despite its intent, might inadvertently benefit large platforms like Google by increasing compliance costs for smaller rivals, as large entities can leverage their extensive resources to absorb these costs and potentially become "de facto privacy regulators". However, other examples demonstrate substantial fines levied against major companies such as Amazon and Meta for failing to implement privacy by design and data minimization effectively. This indicates that while large companies may have an initial advantage in terms of compliance resources, they are also under greater scrutiny and face higher penalties for significant violations. This creates a complex environment where data minimization is both a competitive challenge and a critical area of risk for all organizations, regardless of size. True success in this area requires genuine commitment and robust implementation, not merely superficial adherence.
Conclusion and Recommendations
Data minimization is unequivocally more than a mere regulatory hurdle; it stands as a strategic imperative that underpins robust data protection, significantly enhances security, drives operational efficiency, and cultivates invaluable customer trust. As the digital landscape continues to evolve and data privacy becomes an increasingly central concern for individuals and regulatory bodies alike, mastering data minimization is no longer an optional endeavor but an essential component for long-term organizational success and sustainability.
To effectively navigate this landscape and realize the full benefits of data minimization, organizations are advised to adopt the following key recommendations:
Prioritize a Data-First Audit: Systematically map and audit all personal data across the entire organization. This foundational step is critical for gaining a clear understanding of what data is collected, the precise reasons for its collection, where it is stored, and who has access to it.
Define and Document Clear Purposes: For every piece of personal data, explicitly define its specified, explicit, and legitimate purpose. Organizations must rigorously challenge the necessity of each data point, ensuring it is "adequate, relevant, and limited to what is necessary" for that purpose.
Implement Robust Data Lifecycle Management: Establish and rigorously enforce comprehensive data retention policies that specify justified timeframes for different data types. Implement automated processes for data deletion or anonymization once data is no longer needed for its original purpose.
Embed Privacy by Design and Default: Integrate data minimization principles into the design and development of all new systems, products, and processes from their inception. This includes ensuring privacy-friendly default settings and proportional data collection mechanisms from the outset.
Leverage Privacy-Enhancing Technologies (PETs): Explore and strategically implement PETs such as pseudonymization, anonymization, synthetic data generation, differential privacy, and homomorphic encryption. These technologies enable organizations to minimize identifiable data while retaining its utility for analysis, innovation, and other legitimate business functions.
Foster a Culture of Privacy: Provide continuous and comprehensive training and awareness programs for all employees on data minimization principles, secure data handling practices, and their individual roles in maintaining compliance. Strong leadership commitment is crucial for driving and sustaining this essential cultural shift throughout the organization.
Regularly Review and Adapt: Data minimization is an ongoing journey, not a one-time achievement. Periodically review data collection practices, retention policies, and security measures to ensure they remain relevant, adequate, and compliant with evolving legal and business requirements.
Proactive Engagement with Regulators: Maintain clear and accurate records of all processing activities and be prepared to demonstrate compliance at any time. Respond promptly and transparently to any regulatory inquiries or data incidents to mitigate potential penalties and maintain a positive relationship with supervisory authorities.
By embracing and rigorously implementing these strategies, organizations can not only meet their GDPR obligations but also unlock significant business advantages, positioning themselves as trusted and responsible stewards of personal data in the increasingly data-driven digital age.
Conclusion
Data minimization represents more than merely a compliance requirement—it offers a strategic opportunity to fundamentally transform how organizations approach data governance. By collecting and retaining only what is necessary, businesses can simultaneously reduce risks, cut costs, improve operational efficiency, and build stronger trust relationships with increasingly privacy-conscious stakeholders. Our exploration of implementation strategies demonstrates that effective data minimization requires thoughtful planning, cross-functional collaboration, and ongoing refinement rather than one-time policy changes. Organizations that approach minimization systematically—starting with comprehensive data mapping, implementing purposeful collection practices, designing privacy-centric systems, applying tiered access models, and maintaining robust retention management—create sustainable competitive advantages beyond mere regulatory compliance.
The challenges of implementation, while real, prove surmountable through methodical approaches that balance compliance needs with business functionality. Legacy systems can be adapted through compensating controls, cultural resistance can be overcome through education and leadership support, and business requirements can be accommodated through targeted minimization techniques that preserve analytical capabilities while reducing privacy risks. Perhaps most importantly, data minimization aligns with broader digital transformation imperatives, prompting organizations to move from indiscriminate data accumulation toward strategic, value-driven information management. As regulatory scrutiny intensifies and data volumes continue growing exponentially, the organizations that thrive will be those that master the art of doing more with less—extracting maximum value from minimal necessary data. By implementing the strategies outlined in this guide, your organization can join the forward-thinking businesses transforming regulatory requirements into operational strengths, creating leaner, more agile data practices that serve both compliance objectives and business goals.
Frequently Asked Questions
What is data minimization under GDPR? Data minimization is a fundamental principle under GDPR Article 5(1)(c) requiring that personal data be "adequate, relevant and limited to what is necessary" for the specific purposes for which it's processed. This principle prohibits the collection of excessive data "just in case" it might be useful later, requiring organizations to justify why each data element is necessary for stated processing purposes.
What specific penalties has the GDPR imposed for violations of data minimization? Regulatory authorities have issued several significant fines specifically citing excessive data collection, including a €50 million fine to a major tech company partly for collecting unnecessary data without proper legal basis, a €35.3 million penalty to a retailer for excessive employee monitoring, and multiple smaller fines (€5-15 million range) for retaining customer data beyond necessary periods. Enforcement actions increasingly focus on minimization violations as a primary consideration.
How can businesses determine what data is "necessary" for their purposes? Determining necessity involves establishing clear processing purposes first, then evaluating each data element against objective criteria: Is this specific data element required to accomplish the stated purpose? Would the purpose be impossible or significantly impaired without this data? Is there a less privacy-intrusive alternative? Could the same goal be achieved with anonymized or aggregated data? Organizations should document this analysis to demonstrate compliance.
Does data minimization mean we can't collect data for analytics and business intelligence? No, data minimization doesn't prohibit analytics but requires more thoughtful approaches. Organizations can conduct robust analytics while respecting minimization through techniques like using anonymous or aggregated data, employing pseudonymization to protect individual identities while maintaining analytical utility, implementing privacy-preserving computation methods, or using synthetic data that maintains statistical properties without compromising real individuals' privacy.
How does data minimization relate to AI and machine learning applications? Data minimization presents unique challenges for AI/ML applications that traditionally rely on large datasets. However, emerging approaches like federated learning (where models are trained across multiple devices without centralizing data), differential privacy techniques that add calibrated noise to datasets, and synthetic data generation allow organizations to develop AI solutions while respecting minimization principles. The key is clearly documenting why specific data elements are necessary for model functionality.
What are the most effective technical approaches to implement data minimization? Effective technical implementations include data field-level controls that prevent collection of unnecessary fields, attribute-based access control that limits data visibility based on purpose and need-to-know, dynamic data masking that shows only required information to specific users, automated retention enforcement through technical controls, and privacy engineering approaches that embed minimization directly into system architecture rather than adding it afterward.
How should organizations handle legitimate business requirements that seem to conflict with minimization? When facing apparent conflicts between business needs and minimization, organizations should first challenge whether full data is truly necessary by testing with reduced datasets. If certain elements prove essential, consider techniques like pseudonymization to reduce privacy impact, implement stricter access controls and purpose limitations for sensitive data, create stronger justification documentation, and establish elevated approval processes for exceptions to standard minimization practices.
Does implementing data minimization affect our obligations regarding data subject requests? Data minimization significantly simplifies compliance with data subject requests. With less data collected and clearer purpose documentation, organizations can more efficiently locate relevant information, provide more comprehensive access to all relevant data, implement erasure requests more completely, and respond to portability requirements more easily. A minimized data footprint naturally reduces the scope and complexity of these obligations.
How does data minimization benefit cybersecurity efforts? Data minimization provides substantial security benefits by reducing the attack surface available to potential attackers. With less sensitive data stored, the impact of successful breaches is naturally limited. Additionally, minimization forces clearer data organization and governance, which improves visibility into data assets and enables more targeted security controls, reduces the complexity of encryption requirements, and can eliminate unnecessary data flows that create security vulnerabilities.
What industries benefit most from implementing data minimization strategies? While all sectors benefit from data minimization, organizations in highly regulated industries like healthcare, financial services, and insurance see particularly substantial advantages through reduced compliance overhead and lower breach impacts. Organizations processing large volumes of customer data, including retailers and technology companies, benefit through significant storage cost reductions and improved customer trust. Public sector entities benefit through enhanced transparency and better citizen service delivery with minimized privacy intrusion.
Additional Resources
GDPR Compliance In-Depth Insights - Comprehensive guide to all aspects of GDPR compliance, including the role of data minimization within the broader compliance framework.
The Purpose of GDPR: Safeguarding Data Privacy - Detailed exploration of the core principles underlying GDPR, helping organizations understand the rationale behind requirements like data minimization.
Key Principles of GDPR: Safeguarding Data Privacy - In-depth analysis of the seven GDPR principles, including data minimization, lawfulness, transparency, and accountability.
Data Protection and Privacy for Businesses and Individuals - Practical guidance on implementing effective data protection measures that balance business needs with privacy rights.
Privacy Impact Assessment (PIA) - Guide to conducting Privacy Impact Assessments that incorporate data minimization principles from the design phase of projects and systems.
