GDPR Compliance Checklists for SMEs
Compare GDPR, CCPA, LGPD, and PIPL data protection laws. Understand key differences, compliance requirements, and penalties across global privacy regulations for businesses operating internationally.


The General Data Protection Regulation (GDPR), enacted in 2018, represents a landmark in data privacy, offering robust protections for EU citizens' data. For Small and Medium-sized Enterprises (SMEs), however, navigating this regulatory landscape has presented significant challenges. Unlike larger corporations with extensive legal and compliance departments, SMEs often grapple with limited resources, a knowledge gap regarding complex legal requirements, and the substantial financial burden associated with compliance. This report provides a comprehensive, actionable checklist designed to guide SMEs through the intricacies of GDPR compliance, emphasizing foundational principles, practical implementation steps, and strategies for leveraging available resources. It also addresses the ongoing European Commission initiatives aimed at simplifying administrative burdens, clarifying that while procedural ease may be on the horizon, the core tenets of data protection remain non-negotiable. By adopting a proactive and structured approach, SMEs can transform compliance from a daunting obligation into a strategic advantage, fostering trust, enhancing security, and supporting sustainable growth.
1. Introduction: Navigating GDPR for Small and Medium-sized Enterprises
The General Data Protection Regulation (GDPR) has profoundly reshaped how organizations handle personal data since its implementation in 2018. It has established unprecedented protections for the data of EU citizens, yet this comprehensive framework has simultaneously introduced significant compliance challenges, particularly for Small and Medium-sized Enterprises (SMEs). This duality positions GDPR as both a vital safeguard for individual privacy and a considerable regulatory hurdle for businesses.
SMEs frequently encounter unique obstacles in achieving and maintaining GDPR compliance. Unlike their larger counterparts, which typically possess dedicated legal and compliance departments, SMEs often lack the necessary internal resources—both financial and human—to effectively manage the intricate documentation, record-keeping, and technical requirements mandated by the regulation. This resource disparity often forces small business owners into a difficult choice between allocating critical time and financial resources to compliance efforts or directing them towards business development and innovation, creating an unsustainable tension.
A primary challenge for SMEs is simply comprehending the full scope of the regulation and its specific impact on their operations. A prevalent and potentially perilous misconception among many SME owners is that their smaller size might exempt them from certain GDPR requirements, leaving them vulnerable to substantial compliance failures and associated penalties. The extraterritorial reach of GDPR further complicates matters, as it applies not only to businesses physically located within the European Economic Area (EEA) but also to those offering goods or services to EEA residents or monitoring their behavior, irrespective of the business's geographical location. This means a small online retailer based outside the EU, for instance, could still be subject to GDPR if it serves European customers.
The economic impact of GDPR compliance on SMEs is substantial. Figures indicate that compliance costs for companies adhering to children's data protection rules can range from €500,000 for SMEs. The consequences of non-compliance are severe, including maximum fines that can reach 4% of an organization's global annual turnover or €20 million, whichever is higher. Beyond financial penalties, data breaches and non-compliance can lead to significant damage to reputation, loss of customer trust, legal challenges, and extensive regulatory investigations.
The inherent structural limitations of SMEs, such as limited resources and specialized knowledge, can make them disproportionately vulnerable to the negative impacts of non-compliance. This situation highlights that a smaller size is not a shield against GDPR obligations but can often translate into a compliance liability due to the challenges in dedicating sufficient internal capacity. Consequently, external support—whether from consultants, compliance software, or official guidance—becomes not merely beneficial but frequently critical for SMEs to bridge the resource and knowledge gap. Proactive engagement with these external resources can transform a potential liability into a manageable risk, underscoring that a purely self-managed approach may be insufficient for comprehensive compliance.
2. GDPR Fundamentals for SMEs: Key Concepts and Principles
Understanding the foundational terminology and principles of GDPR is paramount for any SME embarking on its compliance journey. These core concepts form the bedrock upon which all compliance efforts are built.
Defining Essential GDPR Terminology
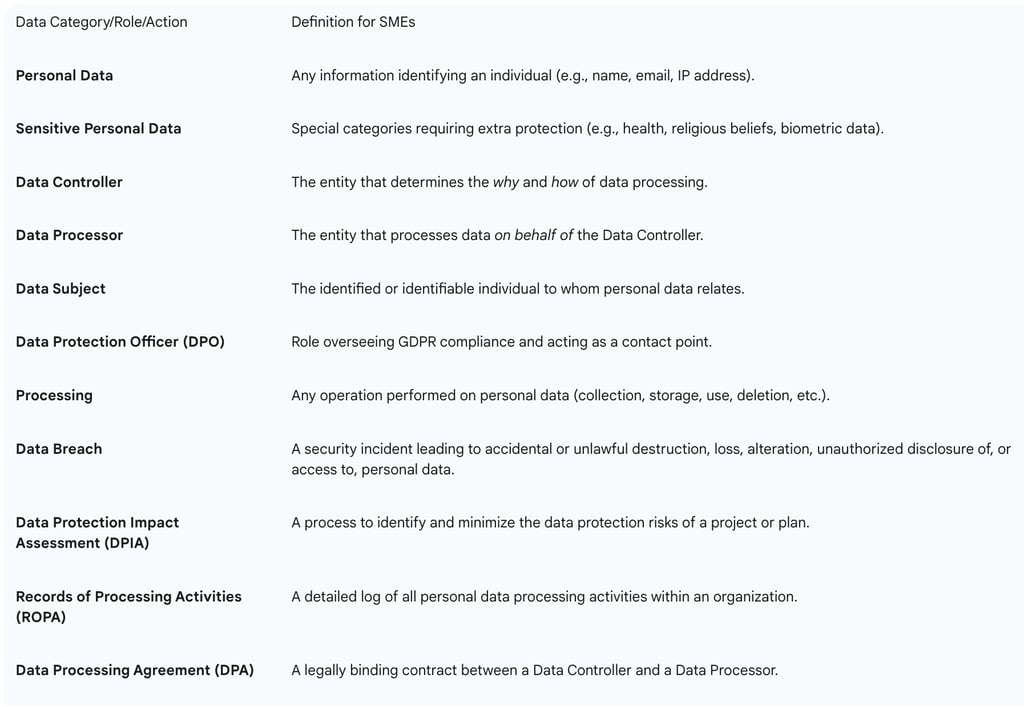
The GDPR introduces specific terms that are crucial for comprehending its requirements:
Personal Data: This refers to any information that can directly or indirectly identify an individual, known as a Data Subject. Examples include names, email addresses, phone numbers, physical addresses, photos, bank account numbers, or social media handles. A subset,
Sensitive Personal Data, includes information related to racial or ethnic origin, political opinions, religious or philosophical beliefs, trade union membership, genetic data, biometric data (for unique identification), health data, or data concerning a person's sex life or sexual orientation. Such sensitive data requires heightened protection.
Data Controller: This is the individual or company that determines the purpose, means, and conditions of personal data processing. The data controller decides
why and how data is processed.
Data Processor: This is an entity that processes personal data on behalf of the data controller, typically an external company or service provider. Data processors are legally obligated to process data only according to the documented instructions provided by the data controller.
Processing: This term encompasses any operation or set of operations performed on personal data, whether by automated means or not. This includes collection, recording, organization, structuring, storage, adaptation or alteration, retrieval, consultation, use, disclosure by transmission, dissemination or otherwise making available, alignment or combination, restriction, erasure, or destruction.
Data Protection Officer (DPO): This is a designated role responsible for overseeing the organization's data protection strategy and ensuring compliance with applicable data protection rules. The DPO serves as a key point of contact for supervisory authorities and data subjects.
To provide a clear and accessible foundation, the following table summarizes these essential terms:
Core Data Protection Principles
Beyond terminology, GDPR is built upon a set of fundamental data protection principles that apply universally, regardless of an organization's size. These principles are unlikely to change, even with future simplification efforts, as they are rooted in fundamental EU rights.
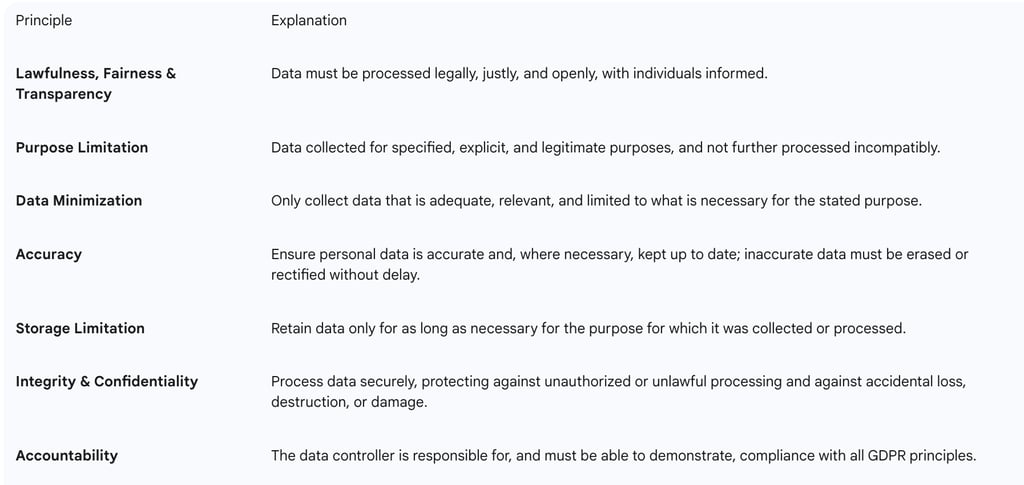
Lawfulness, Fairness, and Transparency: Personal data must be processed lawfully, fairly, and transparently in relation to the individual. This means individuals have the right to be informed about how their data is being used.
Purpose Limitation: Personal data must be collected for specified, explicit, and legitimate purposes and not further processed in a manner that is incompatible with those purposes.
Data Minimization: Only personal data that is adequate, relevant, and limited to what is necessary for the stated purpose should be collected and processed. Organizations should avoid collecting unnecessary information.
Accuracy: Personal data must be accurate and, where necessary, kept up to date. Every reasonable step must be taken to ensure that inaccurate personal data is erased or rectified without undue delay.
Storage Limitation: Personal data can only be kept for as long as it is necessary for the purpose for which it was collected or processed.
Integrity and Confidentiality: Personal data must be processed securely, protecting against unauthorized or unlawful processing and against accidental loss, destruction, or damage, using appropriate technical or organizational measures.
Accountability: The data controller is responsible for, and must be able to demonstrate, compliance with all GDPR principles.
The following table provides a concise explanation of these core principles:

These tables are crucial because GDPR introduces specific, legally defined terminology and principles that are central to understanding compliance. For SMEs, who may lack extensive legal expertise or dedicated compliance departments , a clear, concise glossary and explanation of principles provide an immediate and accessible foundation. Without a solid understanding of these terms and principles, subsequent checklist items and underlying requirements would remain abstract and difficult for business owners or managers to apply effectively. This approach directly addresses the challenge of "Understanding GDPR Basics for SMEs" by breaking down the initial knowledge barrier and helping organizations grasp the "spirit" and underlying intent of the law.
3. The Comprehensive GDPR Compliance Checklist for SMEs: Actionable Steps
Achieving GDPR compliance requires a structured and systematic approach. This section outlines a practical 10-step checklist, integrating essential actions and considerations for SMEs to navigate the regulatory landscape effectively.
3.1. Data Mapping and Records of Processing Activities (ROPA)
The initial step in GDPR compliance involves a thorough understanding of the data an organization handles. This requires conducting a comprehensive data audit to identify and categorize all personal data processed. The audit should meticulously map out where data is stored, how it is collected, who has access to it, and how long it is retained. This systematic process is vital for uncovering potential risks, identifying redundant data, and pinpointing non-compliant practices, thereby providing a holistic view of the organization's data ecosystem.
A critical output of this process is the creation and maintenance of a Records of Processing Activities (ROPA). This log, mandated by GDPR, should detail precisely what personal data is held, its origin, with whom it is shared, and the specific activities performed with it. The ROPA must be kept in electronic form and be readily accessible to regulatory authorities upon request. Establishing procedures to share this information with relevant stakeholders and ensuring its continuous update to reflect ongoing changes in data processing activities is also essential.
The consistent emphasis on creating and maintaining detailed records, such as ROPAs, consent records, breach registers, privacy policies, Data Protection Impact Assessments (DPIAs), Legitimate Interest Assessments (LIAs), and contracts with processors, underscores a fundamental aspect of GDPR: accountability. The regulation defines accountability as the ability to demonstrate compliance with GDPR requirements through relevant documentation. This means that merely adhering to compliance in practice is insufficient; an organization must be able to
prove its compliance to regulatory bodies or data subjects. Documentation serves as the primary, legally recognized evidence. Without proper records, even if an SME follows all rules, it cannot effectively defend itself against regulatory inquiries or potential fines, making the absence of documentation itself a compliance failure. This elevates documentation from a mere bureaucratic task to a critical legal and operational safeguard. This requirement, while contributing to the administrative burden on SMEs , also highlights the value of technology solutions and readily available templates that can automate or simplify record-keeping, making demonstrable accountability achievable even for resource-constrained businesses.
3.2. Establishing Lawful Bases for Data Processing
Every instance of personal data processing must be underpinned by a lawful basis as stipulated by GDPR. Organizations must determine and document the specific legal grounds for each data processing activity. GDPR provides several lawful bases, including the data subject's consent, contractual necessity, legitimate interest, legal obligation, vital interests, or public task.
If consent is chosen as the legal basis, robust and verifiable procedures must be established for its obtainment and management. Consent must be freely given, specific, informed, and unambiguous. This often involves users actively agreeing, for example, through a clear cookie consent banner, and being able to easily withdraw their consent at any time. Comprehensive records of consent, including the date, method of obtainment, and the specific information provided to the individual at the time of consent, must be securely maintained.
When relying on legitimate interests as the lawful basis, organizations are required to conduct a Legitimate Interests Assessment (LIA). This assessment helps justify the decision to process data under legitimate interests, ensuring that the organization has thoroughly considered and protected the rights and interests of individuals. The LIA should be documented and regularly reviewed, especially if circumstances change.
3.3. Privacy Policies and Transparency
Transparency is a cornerstone of GDPR. Organizations must update or create privacy policies that clearly and concisely communicate how personal data is collected, utilized, and stored. These policies should encompass key areas such as data subject rights, data retention periods, the organization's legal obligations, and relevant contact details for individuals.
The privacy notice, which is often part of the privacy policy, must be concise, intelligible, easily accessible, and free of charge. It should be written in clear and plain language, particularly when addressing children. Furthermore, it should explain the risks associated with data processing and the safeguards the organization has implemented. For optimal accessibility, a link to the privacy policy should be prominently displayed, typically in the website footer, and wherever personal information is collected, such as on sign-up forms, checkout screens, or within email communications.
3.4. Implementing Robust Data Protection Measures and Security
Safeguarding personal data against unauthorized access, breaches, and loss is a continuous obligation under GDPR. Organizations must adopt strong technical and organizational measures to ensure a level of security appropriate to the risk involved. These measures may include data encryption, secure access controls, regular vulnerability assessments, and pseudonymization of personal data where appropriate to reduce identification risks
Building privacy by design into systems and processes is crucial. This involves ensuring that systems minimize data collection, restrict access to authorized personnel, and allow data subjects control over their information. Organizations should continuously review and enhance their data security features and controls.
The concept of "security measures" under GDPR is holistic, extending far beyond mere technical IT solutions. While technical safeguards like encryption, secure access controls, and vulnerability assessments are vital, the regulation implicitly mandates a multi-layered defense. Evidence from various sources indicates that effective security also encompasses human behavior, internal procedures, and a proactive approach to risk management. This includes providing comprehensive staff training , establishing clear information security policies and procedures , and developing robust data breach response plans that define roles, procedures, and testing protocols. Common incidents such as phishing attacks or misplaced devices often stem from human or procedural vulnerabilities, not solely technical failures. Therefore, for SMEs, security compliance necessitates a multi-faceted strategy. It is insufficient to simply deploy security software; organizations must also invest in thorough training for their employees, develop clear internal policies and procedures, and regularly test their preparedness for security incidents. This comprehensive approach fosters a resilient "culture of security" within the organization, which is far more effective and compliant than relying solely on technological tools.
3.5. Managing Data Subject Rights
GDPR grants individuals several fundamental rights concerning their personal data, and organizations must establish efficient mechanisms to handle requests related to these rights within legally mandated timeframes, typically one month.
Key rights include:
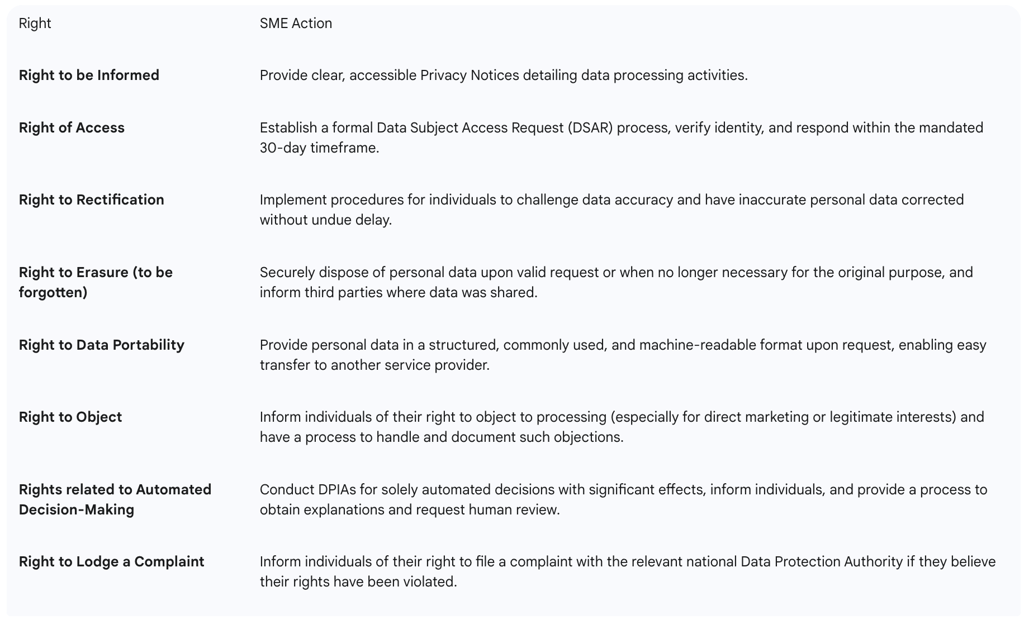
Right to be informed: Individuals have the right to know how and why their personal data is processed.
Right of access: Individuals can obtain a copy of their personal data held by the organization.
Right to rectification: Individuals have the right to have inaccurate personal data corrected without undue delay.
Right to erasure (Right to be forgotten): Individuals can demand the deletion of their data without undue delay if there is no compelling reason for the organization to continue processing it.
Right to data portability: Individuals can obtain and reuse their personal data across different services in a structured, commonly used, and machine-readable format.
Right to object: Individuals can object to the processing of their personal data, particularly for direct marketing or when processing is based on legitimate interests.
Rights related to automated decision-making and profiling: Individuals have the right not to be subject to decisions based solely on automated processing, including profiling, that produce legal or similarly significant effects concerning them.
Right to submit a complaint: Individuals have the right to file a complaint with a data protection authority if they believe their rights have been violated.
Organizations must implement a clear process for handling Data Subject Access Requests (DSARs). This process should include establishing internal responsibilities, verifying the identity of the requester, efficiently locating relevant personal data, compiling a comprehensive answer within the 30-day timeframe, and meticulously documenting all communication with the individual for accountability purposes.
The following table outlines these rights and the corresponding actions SMEs should take:

This table directly addresses a core and frequently interactive component of GDPR: the rights of individuals. For SMEs, understanding and operationalizing these rights can be particularly complex and resource-intensive, as they require specific internal processes and timely responses. This table simplifies the information by clearly linking each specific right to a concrete, actionable step or procedure the SME needs to implement. It serves as an immediate, practical reference point for compliance officers and employees, ensuring that the business is prepared to handle common data subject requests, which are a frequent point of interaction and potential non-compliance.
3.6. Data Protection Officer (DPO) Considerations
The appointment of a Data Protection Officer (DPO) is a significant GDPR requirement for certain organizations. A DPO must be designated if an organization's core activities involve large-scale processing of sensitive data or regular and systematic monitoring of data subjects. The DPO's responsibilities include monitoring data protection practices, advising on regulatory obligations, and serving as the primary point of contact for data protection authorities and data subjects.
For SMEs, the requirement to appoint a DPO can be particularly challenging due to resource constraints and the specialized skillsets required. Smaller businesses may find it more practical and cost-effective to appoint an external DPO to fulfill this role. Regardless of whether the DPO is internal or external, their details must be registered with the relevant national Data Protection Authority. Even if a DPO is not strictly mandated, it is considered a best practice for SMEs to nominate a dedicated data protection lead to oversee compliance efforts.
3.7. Engaging with Third-Party Data Processors and Data Processing Agreements (DPAs)
In today's interconnected business environment, most SMEs engage with third-party data processors—entities that process personal data on their behalf, such as cloud service providers, payment gateways, or marketing agencies. GDPR mandates that a written Data Processing Agreement (DPA) must be in place whenever a data controller uses a data processor. This is a fundamental legal requirement; it is unlawful for a data controller to engage a processor without such an agreement.
A DPA is a legally binding contract that clarifies the responsibilities and liabilities between the data controller and the data processor. It must explicitly outline the subject matter, duration, nature, and purpose of the processing, as well as the types of personal data involved and the categories of data subjects. Key clauses in a DPA include confidentiality obligations, specific technical and organizational security measures to be implemented by the processor, requirements for engaging sub-processors (which typically require prior written authorization from the controller), provisions for how data is handled upon contract termination (e.g., deletion or return to the controller), and audit rights for the controller to verify compliance.
For any personal data transferred outside the European Economic Area (EEA), organizations must ensure an adequate level of protection. This typically involves implementing appropriate safeguards, such as the European Commission's Standard Contractual Clauses (SCCs), and meticulously documenting these security arrangements within the written contract.
3.8. Data Breach Preparedness and Response
Despite robust security measures, data breaches can occur. Therefore, developing a comprehensive data breach response plan is a critical component of GDPR compliance. This plan should clearly outline the steps an organization will take in the event of a breach, covering detection, reporting, containment, eradication of the root cause, and mitigation of potential harm.
Timely notification is paramount under GDPR. Organizations are legally required to inform the relevant supervisory authority within 72 hours of becoming aware of a personal data breach. If the breach is severe and poses a high risk to the rights and freedoms of individuals, the affected individuals must also be informed without undue delay. Organizations must maintain thorough records of all breaches, including the facts surrounding the incident, its impact, and the actions taken to contain and resolve the issue, documenting these in a dedicated breach register.
Regular training sessions for employees on how to recognize and report breaches are essential. Furthermore, conducting periodic breach simulations or mock drills is highly recommended to test the effectiveness of the response plan and identify any gaps or areas for improvement.
3.9. Ongoing Accountability and Regular Audits
GDPR compliance is not a one-time event but an ongoing commitment requiring continuous vigilance and adaptation. Organizations must perform regular internal audits to assess their adherence to GDPR requirements. These audits should systematically evaluate the effectiveness of existing data protection measures, identify areas requiring improvement, and ensure that policies and procedures remain current and relevant.
Demonstrating compliance hinges on maintaining a robust data protection policy that is formally approved by management, widely published, and regularly reviewed. Monitoring compliance with these policies and periodically testing the effectiveness of data handling and security controls provides crucial assurances.
Effective information risk management is also vital. Organizations should manage information risks in a structured manner, maintaining a risk register to log identified threats, vulnerabilities, and potential impacts related to their business activities and information assets. Controls should be applied to mitigate identified risks within agreed-upon appetites, and these controls must be regularly tested to ensure their continued effectiveness.
Organizations must also understand when a Data Protection Impact Assessment (DPIA) is required. DPIAs are mandatory for processing operations that are likely to result in a high risk to the rights and freedoms of individuals, particularly when new technologies are involved or for automated decision-making with significant effects. A DPIA must be conducted
before commencing such projects. The process should involve consultation with the Data Protection Officer (DPO) and, where appropriate, with the public or their representatives. If a DPIA indicates that processing would result in a high risk that cannot be mitigated by reasonable means, the business must consult with its national Data Protection Authority prior to commencing the processing.
3.10. Staff Training and Awareness
Human error remains a significant factor in data breaches and compliance failures. Therefore, comprehensive staff training and ongoing awareness programs are indispensable for GDPR compliance. Employees must be educated on GDPR principles, specific data handling procedures relevant to their roles, and the overarching importance of protecting personal data.
Training should include induction programs for new hires and regular updates for all staff, delivered through various channels such as intranet articles, circulars, team briefings, and posters. Tailored training sessions can help different departments understand their specific responsibilities, significantly reducing the likelihood of human error leading to non-compliance. Continuous training ensures that awareness remains high across the organization. Beyond formal training, fostering a positive culture of data protection compliance across the entire business is crucial. This involves encouraging personal responsibility and promoting good security behaviors, with management clearly setting out the business's approach to data protection and actively endorsing this culture.
The following list summarizes the 10-step GDPR Compliance Checklist for SMEs:
Conduct a Data Audit & Map Data Flows (ROPA)
Establish Lawful Bases for Processing
Update Privacy Policies & Notices
Implement Data Protection & Security Measures
Appoint a DPO (if required)
Provide Staff Training & Awareness
Obtain & Manage Consent
Enable Data Subject Rights
Prepare a Data Breach Response Plan
Conduct Regular Audits & Ensure Accountability
This table directly fulfills the need for a practical "GDPR Compliance Checklist for SMEs." By presenting the key actions as a concise, numbered list, it provides an immediate, actionable roadmap for SMEs, making the complex process of GDPR compliance digestible and manageable. It serves as a central reference point that can be easily followed by busy SME owners or compliance leads. Each step is a high-level summary of the detailed actions discussed in the preceding subsections, allowing the reader to quickly grasp the overall scope of work required and track their progress.
4. The Evolving Landscape: Upcoming GDPR Simplification Initiatives
The European Commission is actively pursuing a GDPR simplification initiative, recognizing that the current regulatory burden, particularly on SMEs, may be hindering economic growth and innovation within the EU. European Commissioner Michael McGrath has explicitly articulated the objective: to "ease the burden" on smaller organizations while concurrently "preserving the underlying core objective of our GDPR regime". This balanced approach acknowledges the importance of both robust privacy protection and economic vitality. The impetus for this initiative stems partly from reports, such as the Draghi Report on European competitiveness, which identified issues like inconsistent enforcement across member states, fragmentation due to national variations, legal uncertainty for cross-border operations, and high compliance costs, especially for data-intensive industries.
While the full details of the proposed changes are still pending release, several key areas have been identified for potential reform. These include simplifying record-keeping requirements for organizations with fewer than 500 employees, streamlining the maintenance of data processing registries, and creating more efficient processes for conducting Data Protection Impact Assessments (DPIAs). Efforts are also directed towards harmonizing cross-border compliance to reduce fragmentation among member states and standardizing age of consent definitions across the EU. The initial unveiling of this plan was scheduled for April 16 but has been pushed to May 21, 2025, indicating that it remains a high priority for the Commission.
It is crucial to understand that despite this push for simplification, certain foundational aspects of GDPR are highly unlikely to change. These core principles are deeply rooted in fundamental EU rights and are considered non-negotiable. They include the unwavering requirement for a legal basis for processing personal data, adherence to data minimization principles, strict purpose limitation requirements, the preservation of individual rights (such as the right to access, rectification, and erasure of personal data), principles of transparency in data processing, and the necessity for appropriate security measures. The European Commission has clearly stated that its simplification efforts are specifically aimed at administrative burdens, not at diluting these fundamental protections.
This distinction between administrative simplification and unchanging core principles presents a critical dynamic for SMEs. While the how of compliance—the administrative processes and documentation—might become less arduous in the future, the what and why—the fundamental protections and principles of data privacy—will remain constant. Therefore, delaying action on these core principles in anticipation of simplification would be a significant misstep, as non-compliance with these foundational elements will continue to incur severe penalties. The upcoming simplification should be viewed as a future administrative relief, potentially allowing SMEs to reallocate resources from extensive paperwork to growth and innovation. However, their immediate and ongoing focus must remain on understanding, embedding, and diligently upholding these unchanging core principles within their daily operations. This proactive approach ensures fundamental compliance, positions them advantageously regardless of future administrative adjustments, and helps avoid the misconception that small size might lead to exemption from core responsibilities.
5. Leveraging Technology and Resources for Streamlined Compliance
For SMEs navigating the complexities of GDPR, leveraging technology and external resources can significantly streamline compliance efforts, mitigating the challenges posed by limited internal capacity.
GDPR compliance software and tools offer substantial assistance by automating many burdensome tasks. Such software can help organizations automate documentation and record-keeping, efficiently track and respond to data subject requests, maintain compliant data processing records, conduct and document impact assessments, and continuously monitor data processing activities for compliance issues. Specific solutions, like those offered by Termly, provide automated compliance tools, including generators for privacy policies, compliant consent banners, and Data Processing Agreements (DPAs). These tools can save considerable time and help ensure legal requirements are met.
Beyond comprehensive software, a wealth of templates is available for key GDPR-required documents. These include templates for employee GDPR policies, general privacy policies, Data Protection Impact Assessments (DPIAs), Data Processing Agreements (DPAs), and data breach notification letters. Official bodies, such as the UK's Information Commissioner's Office (ICO) and the European Commission, provide standard DPA templates and Standard Contractual Clauses (SCCs) that serve as reliable models for legal agreements.
Official guidance and practical resources specifically tailored for SMEs are also invaluable. The European Data Protection Board (EDPB) offers a dedicated data protection guide for small businesses, covering essential topics such as data protection basics, individual rights, general compliance, and data security. Similarly, national data protection authorities, like the UK's Information Commissioner's Office (ICO), provide specific guidance and resources to assist SMEs. The UK also operates a broader cybersecurity framework, which includes the Data Protection Act 2018 (DPA 2018), the Privacy and Electronic Communications Regulations (PECR), and the National Cyber Security Centre (NCSC), all of which offer guidance and support to organizations on protecting against cyber threats.
For SMEs that lack deep internal expertise in data protection, seeking professional help is often a highly recommended strategy. External experts can conduct thorough data flow audits more efficiently and provide detailed reports on compliance priorities. This external assistance can significantly save time and ensure accuracy, transforming what might otherwise be an overwhelming task for resource-constrained SMEs into a manageable and expertly guided process.
6. Conclusion: Strategic Compliance for Sustainable Growth
GDPR compliance, while presenting initial challenges, offers significant strategic advantages beyond merely avoiding substantial fines and reputational damage. By embracing robust data protection practices, SMEs can foster deeper trust and confidence with their customers and business partners. This commitment to privacy enhances an organization's overall data security posture, making it more resilient against evolving cyber threats. Furthermore, embedding privacy-by-design principles into business processes can spur innovation, leading to more secure and user-centric products and services. By visibly demonstrating adherence to data protection standards, SMEs can differentiate themselves in competitive markets, cultivate stronger, more loyal customer relationships, and ultimately ensure long-term, sustainable growth in an increasingly data-driven global economy.
Based on the comprehensive analysis, the following recommendations are crucial for SMEs to achieve and maintain effective GDPR compliance:
Prioritize Foundational Principles: Organizations should focus intensely on understanding and implementing the core principles of GDPR—such as lawful basis for processing, data minimization, respecting individual rights, and ensuring appropriate security measures. These principles are enduring and form the bedrock of compliance, irrespective of any future administrative simplifications.
Embrace Proactive Documentation: Accountability under GDPR hinges on demonstrable compliance. SMEs must invest in robust data mapping, maintain comprehensive Records of Processing Activities (ROPAs), and keep accurate records for all data processing activities. Leveraging technology solutions and readily available templates can significantly streamline this often-burdensome process.
Cultivate a Privacy-Aware Culture: Implementing comprehensive staff training programs and fostering a positive, organization-wide culture of data protection is paramount. Human error remains a significant risk factor in data breaches, and an informed, vigilant workforce serves as the primary line of defense.
Regularly Assess and Adapt: GDPR compliance should be viewed as an ongoing journey, not a static destination. Organizations must conduct regular internal audits and continuously review their policies and procedures. This proactive approach allows them to adapt to evolving threats, changes in business operations, and any updates in regulatory requirements.
Leverage External Support: For SMEs with limited internal resources and specialized expertise, engaging external data privacy experts or utilizing compliance software solutions is highly advisable. These resources can effectively bridge knowledge gaps, provide efficient and accurate audits, and automate many administrative tasks, transforming GDPR compliance from a daunting challenge into a manageable and strategically integrated business function.
